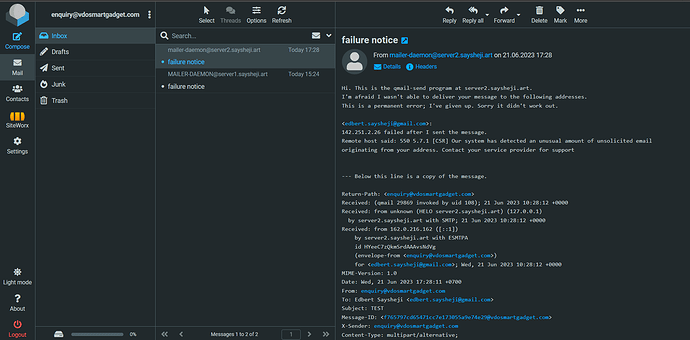
MESSAGE NUMBER 152210:
Received: (qmail 22808 invoked by uid 108); 20 Jun 2023 22:38:14 +0000
Received: from unknown (HELO server.gosys.eu) (127.0.0.1)
by server2.saysheji.art with SMTP; 20 Jun 2023 22:38:14 +0000
Date: Tue, 20 Jun 2023 22:38:14 +0000
Content-Transfer-Encoding: 7bit
Message-ID: 1642627d39506e723d2c2f2130313e363e3d393d2a393c3f3d3278706767777d777a686a7b6e6e795e68414f43474b4a08415a.27791326@zz169.net
Representatives-Violations-Foes: 9C91C27FA
MIME-Version: 1.0
Subject: Complete your debt payment now
To: hautchampsaurd@wanadoo.fr
From: eerfcampshedding@zz169.net
Content-Type: text/html; charset=UTF-8
Axons-Rambling-Uncovered: 8876C1AC
Hi!
I regret to inform you about some sad news for you.
Approximately a month or two ago I have succeeded to gain a total access to all your devices utilized for browsing internet.
Moving forward, I have started observing your internet activities on continuous basis.
Go ahead and take a look at the sequence of events provided below for your reference:
Initially I bought an exclusive access from hackers to a long list of email accounts (in today’s world, that is really a common thing, which can arranged via internet).
Evidently, it wasn’t hard for me to proceed with logging in your email account (hautchampsaurd@wanadoo.fr).
Within the same week, I moved on with installing a Trojan virus in Operating Systems for all devices that you use to login to email.
Frankly speaking, it wasn’t a challenging task for me at all (since you were kind enough to click some of the links in your inbox emails before).
Yeah, geniuses are among us.
Because of this Trojan I am able to gain access to entire set of controllers in devices (e.g., your video camera, keyboard, microphone and others).
As result, I effortlessly downloaded all data, as well as photos, web browsing history and other types of data to my servers.
Moreover, I have access to all social networks accounts that you regularly use, including emails, including chat history, messengers, contacts list etc.
My unique virus is incessantly refreshing its signatures (due to control by a driver), and hence remains undetected by any type of antiviruses.
Hence, I guess by now you can already see the reason why I always remained undetected until this very letter…
During the process of compilation of all the materials associated with you,
I also noticed that you are a huge supporter and regular user of websites hosting nasty adult content.
Turns out to be, you really love visiting porn websites, as well as watching exciting videos and enduring unforgettable pleasures.
As a matter of fact, I was not able to withstand the temptation, but to record certain nasty solo action with you in main role,
and later produced a few videos exposing your masturbation and cumming scenes.
If until now you don’t believe me, all I need is one-two mouse clicks to make all those videos with everyone you know,
including your friends, colleagues, relatives and others.
Moreover, I am able to upload all that video content online for everyone to see.
I sincerely think, you certainly would not wish such incidents to take place, in view of the lustful things demonstrated in your commonly watched videos,
(you absolutely know what I mean by that) it will cause a huge adversity for you.
There is still a solution to this matter, and here is what you need to do:
You make a transaction of 660 USD to my account (an equivalent in bitcoins, which recorded depending on the exchange rate at the date of funds transfer),
hence upon receiving the transfer, I will immediately get rid of all those lustful videos without delay.
After that we can make it look like there was nothing happening beforehand.
Additionally, I can confirm that all the Trojan software is going to be disabled and erased from all devices that you use. You have nothing to worry about,
because I keep my word at all times.
That is indeed a beneficial bargain that comes with a relatively reduced price,
taking into consideration that your profile and traffic were under close monitoring during a long time frame.
If you are still unclear regarding how to buy and perform transactions with bitcoins - everything is available online.
Below is my bitcoin wallet for your further reference: 1PMP68a3iw2X4Ruq2XoENc1jNNaGVELCh6
All you have is 48 hours and the countdown begins once this email is opened (in other words 2 days).
The following list includes things you should remember and avoid doing:
----> qmqtool: remainder of message has been suppressed
That’s actually pretty creepy… but Im not sure if its true all the device is being hacked. Is there any advice for me? Is changing the server password is enough?